Home > Empowering Tips > 10 Phishing Scams You Need to Know

Phishing scams are constantly evolving, becoming increasingly sophisticated and targeted. In our previous article, we covered 8 common phishing examples. Building on insights gathered in 2024, we now present 10 more phishing scams that reflect the latest trends and tactics being used by attackers.
Table of Contents
- 1. Personalized Sextortion Threats
- 2. OneDrive Impersonation Phishing
- 3. FedEx Delivery Notification Scam
- 4. Google Docs Sharing Deception
- 5. Netflix Subscription Expiry Scam
- 6. Fake Social Media Verification Email
- 7. Email Quarantine Fraud
- 8. Fake Meeting Invites
- 9. Impersonated Executive Emails (CEO Fraud)
- 10. False Job Opportunity Offers
- Wrapping Up
1. Personalized Sextortion Threats
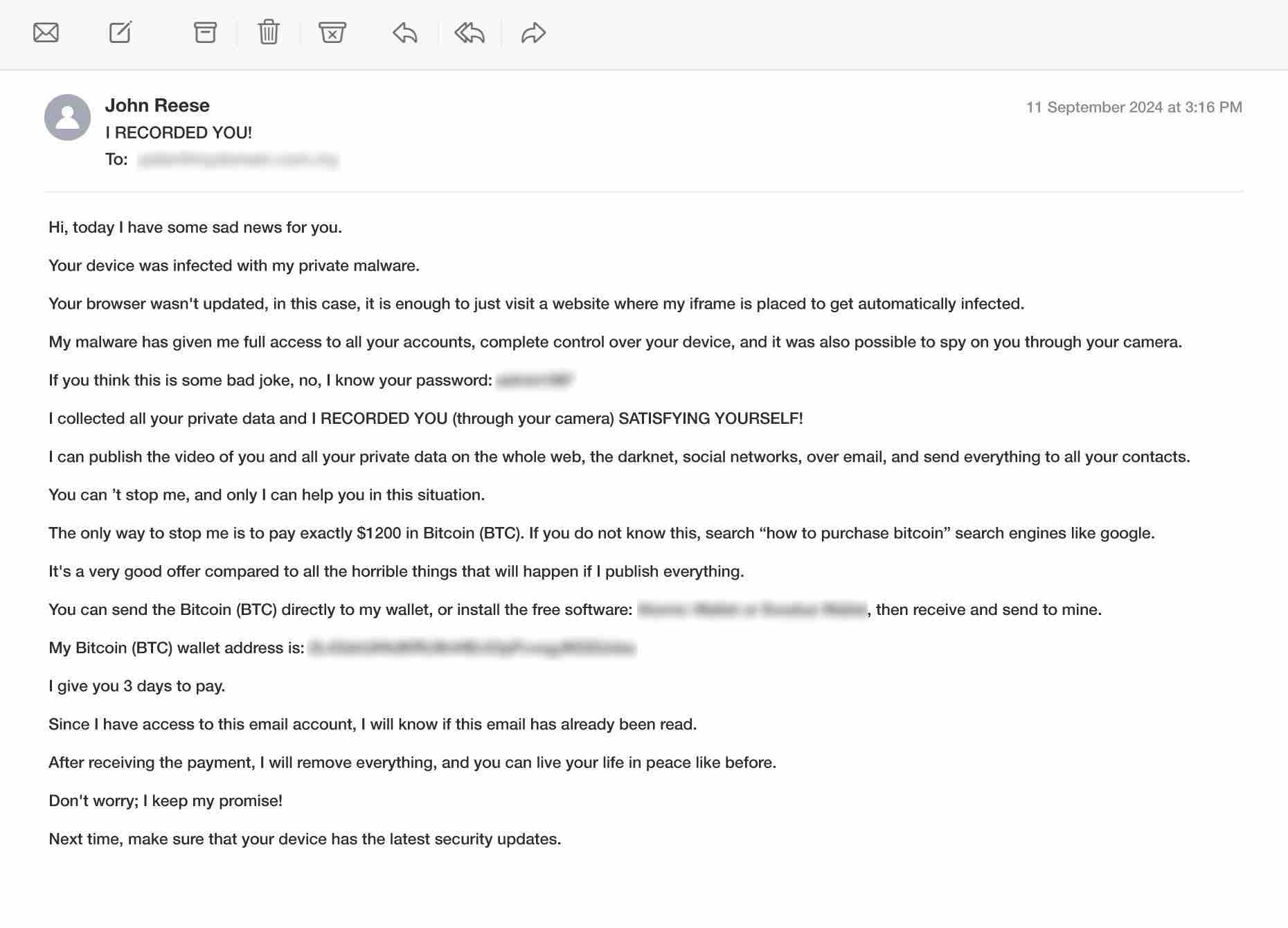
Background: Sextortion emails prey on victim’s fear and embarrassment, claiming to possess compromising personal content such as photos or videos. To create credibility, scammers often include personal data such as passwords obtained from past data breaches. While the claims are fabricated, the inclusion of actual passwords makes the email seem authentic.
How Scammers Use It: The attacker typically demands payment in cryptocurrency to prevent the supposed release of sensitive material to contacts. They may provide fake screenshots or mention specific personal information (e.g., a password) to amplify their threats.
How to Detect:
- Look for vague language, generalized threats, and urgency designed to provoke fear.
- If a password mentioned in the email is familiar, it may have been compromised in a previous breach. Change it immediately if it is still in use.
- Avoid responding to the email or paying the ransom. Instead, report the email to your email service provider or cybersecurity department.
2. OneDrive Impersonation Phishing
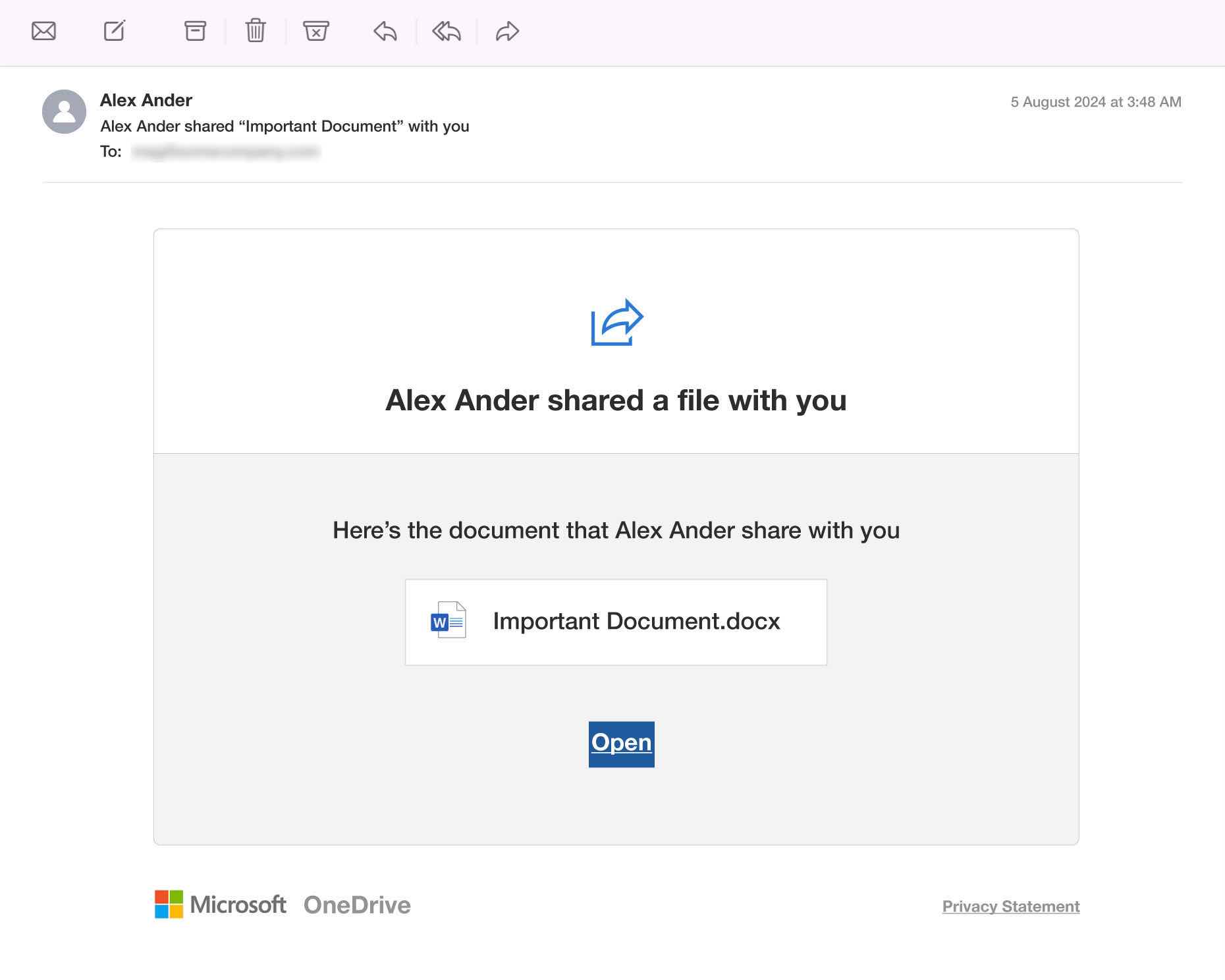
Background: Microsoft OneDrive is a widely-used cloud storage platform, particularly popular among businesses and schools. It allows users to upload, store, and share files securely. When a file or folder is shared, Microsoft sends an email notification to the recipient with details about the sender and a direct link to access the shared item. Legitimate OneDrive notifications come from Microsoft domains, have a clear layout, and link to OneDrive’s official site.
How Scammers Use It: Scammers use OneDrive phishing tactics by mimicking legitimate file-sharing notifications to steal credentials or distribute malware. They often craft professional-looking emails with urgent messaging to prompt victims to click fake links or log into counterfeit Microsoft portals. Victims are particularly vulnerable in collaborative environments, as they may mistake the scam for a legitimate document shared by a colleague or client, acting quickly without verifying the sender or link.
How to Detect:
- Check if the email is from a Microsoft domain (e.g., @onedrive.com or @microsoft.com). Be wary of slight variations in the sender’s address.
- Hover over links before clicking. Authentic OneDrive links should lead to a Microsoft domain like “onedrive.live.com” or “microsoft.com”.
- If you weren’t expecting a shared file, contact the sender directly using known contact details to verify the email’s legitimacy.
3. FedEx Delivery Notification Scam
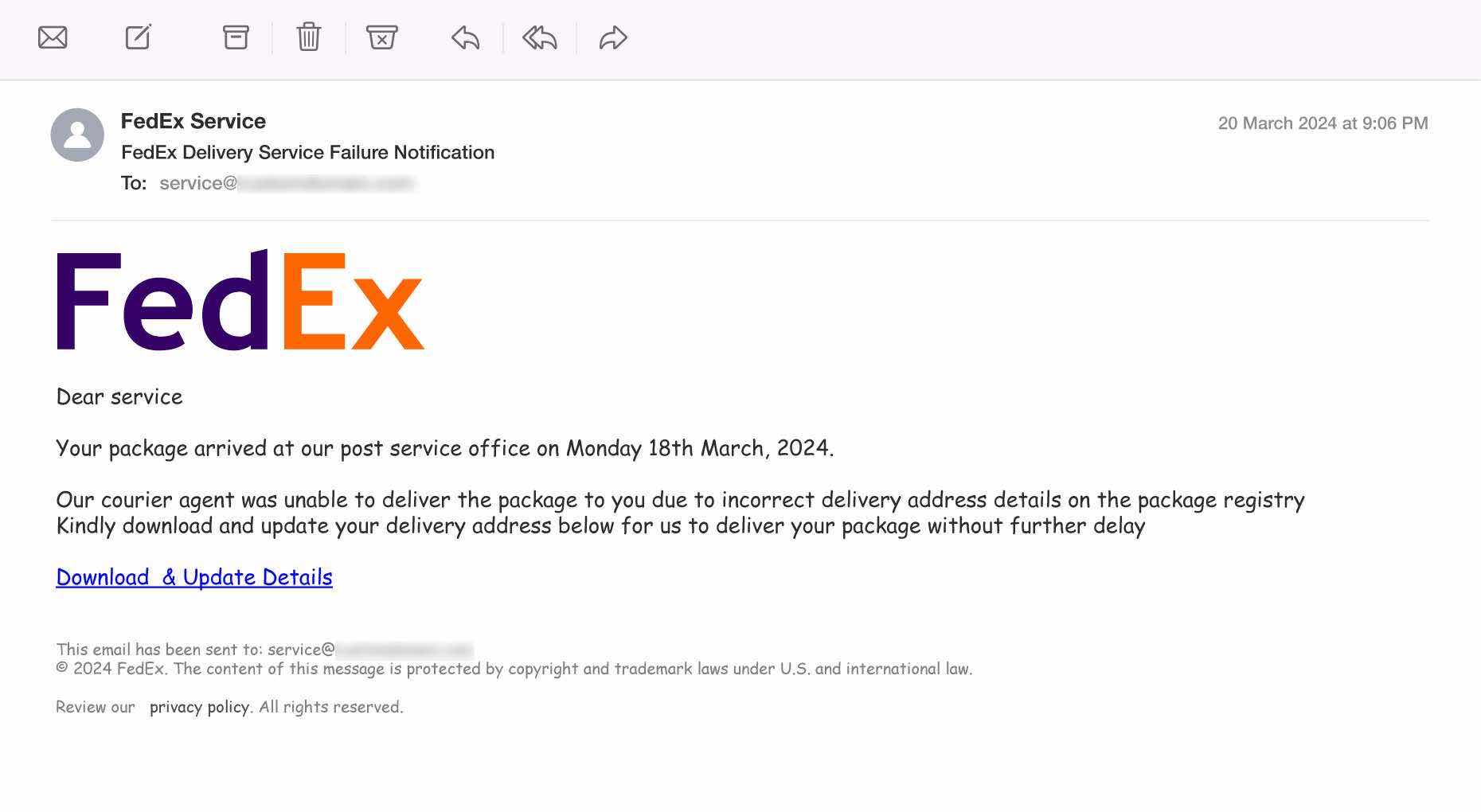
Background: FedEx regularly sends email notifications about shipments, including updates and tracking information. These emails usually contain a tracking number and links to the FedEx website, allowing users to monitor the status of their deliveries.
How Scammers Use It: Scammers exploit this system by creating fake FedEx notifications. The fraudulent emails often claim a package could not be delivered or requires urgent action to avoid delays. Victims expecting a shipment are more likely to believe the email is legitimate and click on malicious links. These links can lead to phishing sites requesting personal or payment information or sites designed to install malware on the victim’s device.
How to Detect:
- Check the sender’s email address carefully. FedEx emails come from legitimate FedEx domains.
- Avoid clicking links in the email. Instead, use the tracking number provided (if any) to check the status on the official FedEx website.
- Be wary of any unsolicited requests for payment or personal details, especially when such information isn’t typically required for package delivery.
4. Google Docs Sharing Deception
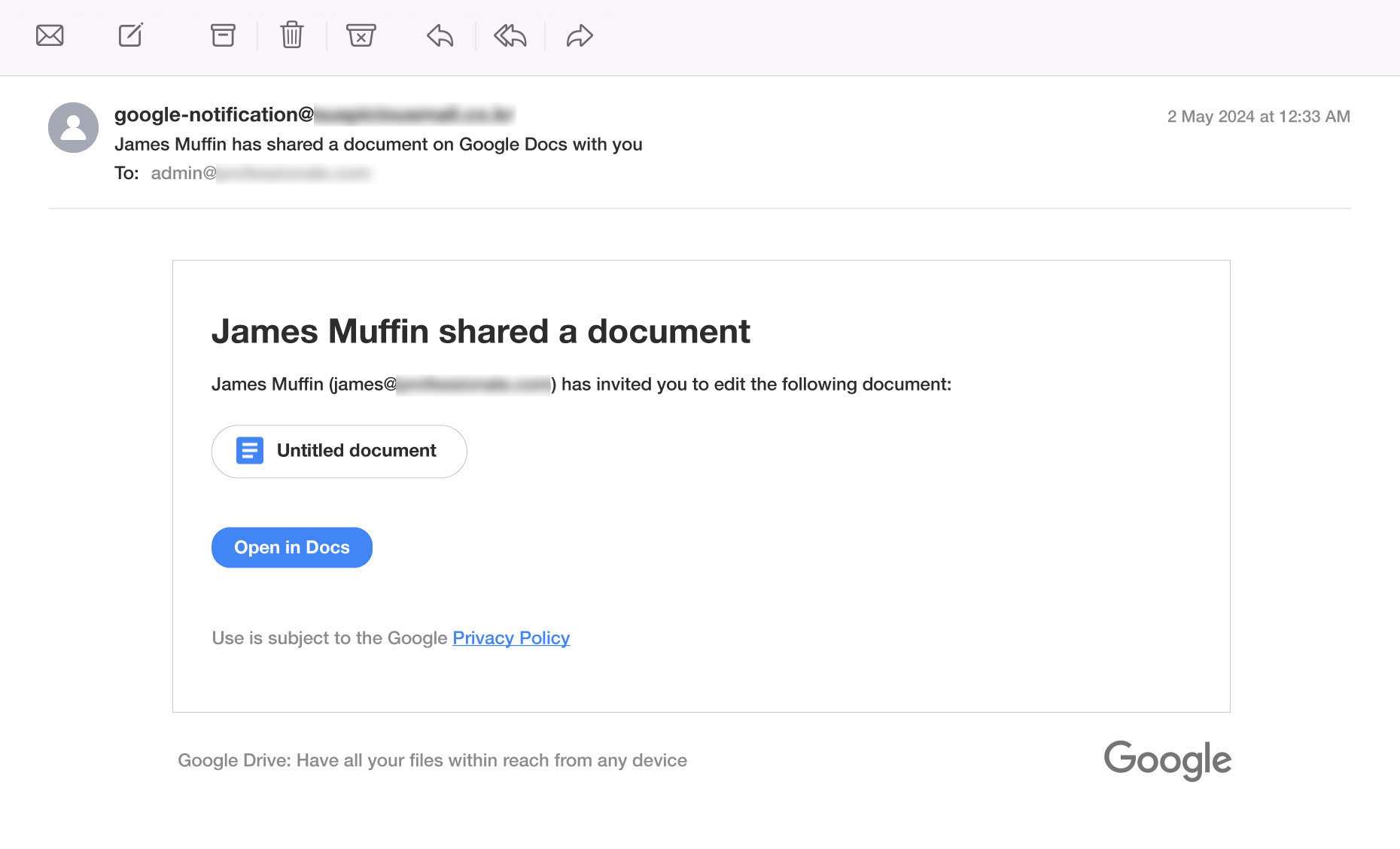
Background: Google Docs is a widely used cloud-based document-sharing platform. Legitimate Google Docs sharing emails typically come from a Google domain (e.g., @gmail.com or @google.com) and notify users when someone has shared a document with them or left a comment. These notifications provide a link to access the document securely.
How Scammers Use It: Scammers exploit Google Docs sharing by sending fake notifications that mimic legitimate emails, often appearing to come from trusted contacts or referencing relevant topics. These emails direct victims to phishing pages that steal login credentials or malware-laden links that compromise devices. Victims are deceived by the professional appearance of the email, their trust in the impersonated sender, and urgency in the message, prompting them to act without verifying its authenticity.
How to Detect:
- Although Google allows users to set up custom email addresses with their own domain, be wary of unfamiliar or slightly altered domain names (e.g., “docs-google.com”).
- Before clicking on any link, hover over it to see the destination URL. Ensure it directs to a legitimate Google domain (docs.google.com).
- If you weren’t expecting a shared document, confirm its legitimacy by contacting the sender through a separate, verified channel.
5. Netflix Subscription Expiry Scam
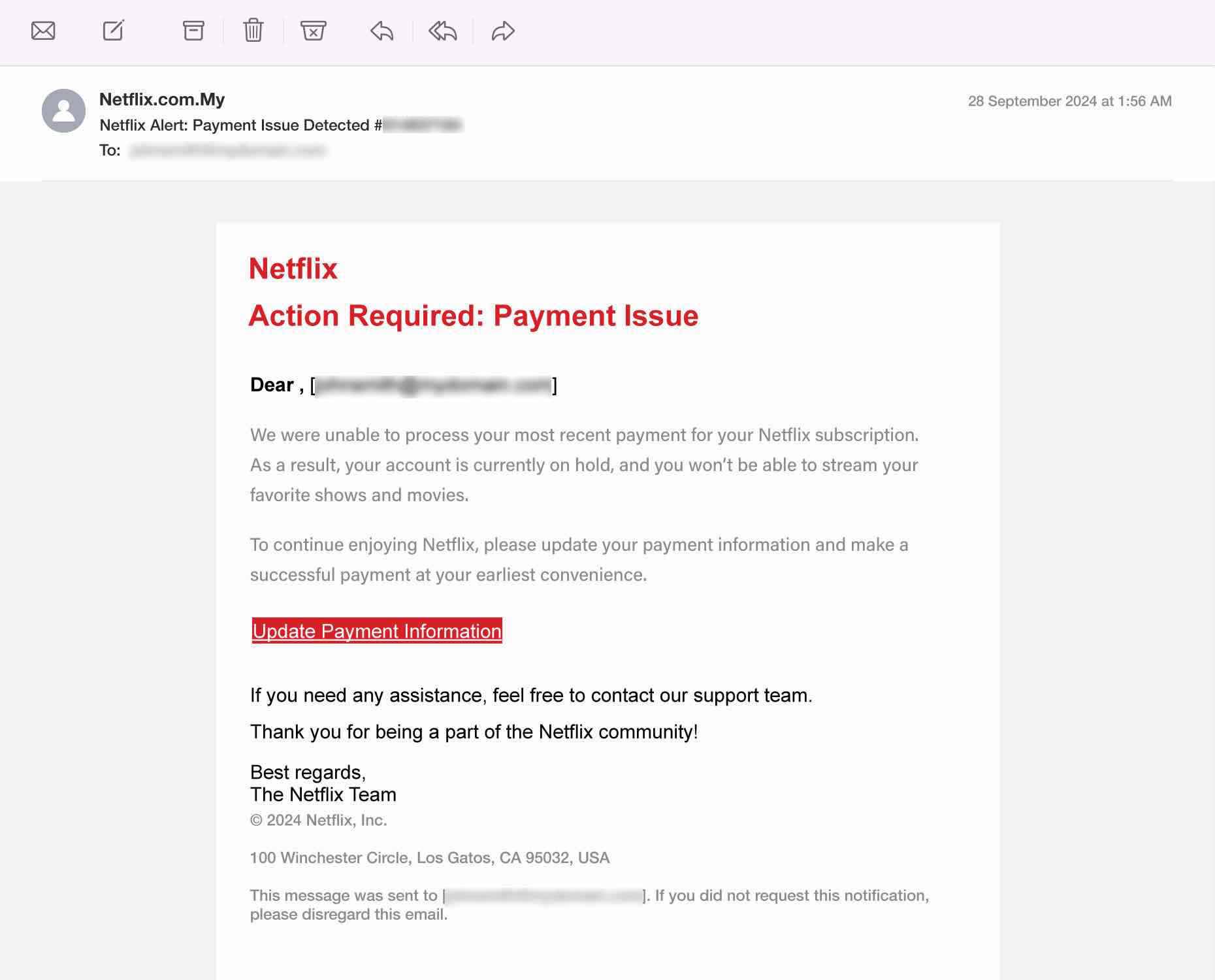
Background: Netflix frequently sends emails to its users regarding their subscription status, payment issues, or account updates. These emails usually come from a verified Netflix domain and contain relevant details about the user’s account. Legitimate emails from Netflix may alert users when their subscription is nearing its end or when there’s an issue with payment methods.
How Scammers Use It: Scammers impersonate Netflix by sending fraudulent emails claiming the user’s subscription has expired or payment has failed. They create a sense of urgency, pressuring users to click a link and update their payment information or resolve the issue to prevent account suspension. These links lead to phishing websites that either steal credit card details or install malicious software.
How to Detect:
- Genuine emails from Netflix come from “@netflix.com” or other official domains. Be cautious of small spelling errors or unusual domain names.
- Instead of clicking on the link in the email, go directly to the Netflix website by typing “netflix.com” into your browser. Log in to your account and check for any subscription issues.
- Phishing emails often contain errors or awkward phrasing that official Netflix communications do not.
6. Fake Social Media Verification Email
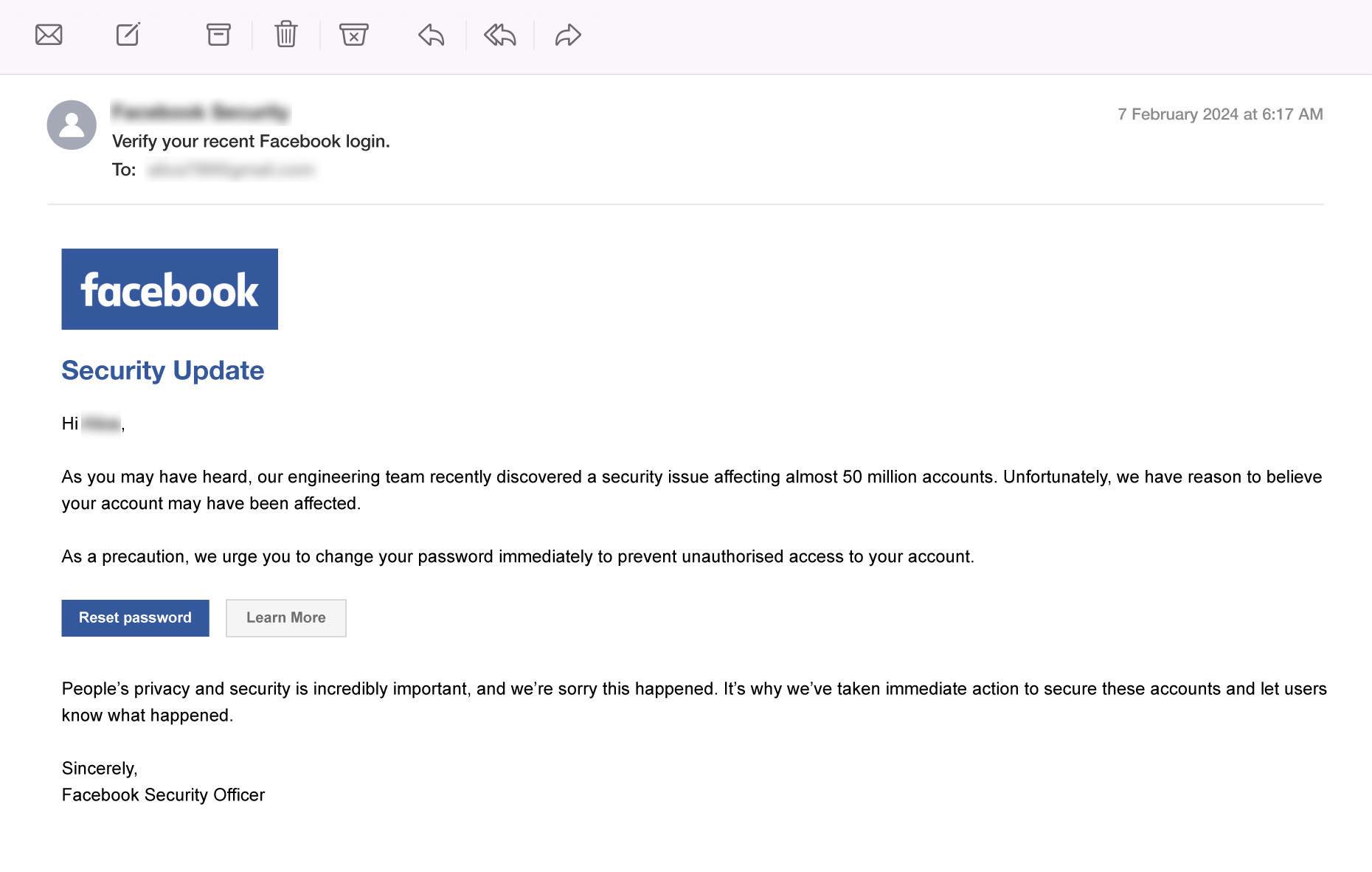
Background: Social media platforms routinely send emails to users when they need to verify their identity or confirm changes to their account settings. Verification emails typically contain a unique code or a direct link to confirm account ownership, especially when resetting passwords or enabling two-factor authentication. These emails come from the official social media domain (e.g., “@facebook.com”).
How Scammers Use It: A typical fake social media verification email might claim that your account has been flagged for suspicious activity or that you need to confirm your identity to avoid account suspension. The email will include a link that appears to lead to the social media login page. However, the link directs victims to a fake page designed to capture their login details, or to a malicious website that installs malware on their device.
How to Detect:
- Always verify the sender’s email address. For example, official emails from Facebook should come from “@facebook.com” or related domains.
- Never click links directly from suspicious emails.
- Check for spelling and grammar in the email content. If it contains poor grammar, unusual phrasing, or typographical errors, it is a red flag that the email may be a phishing attempt.
7. Email Quarantine Fraud
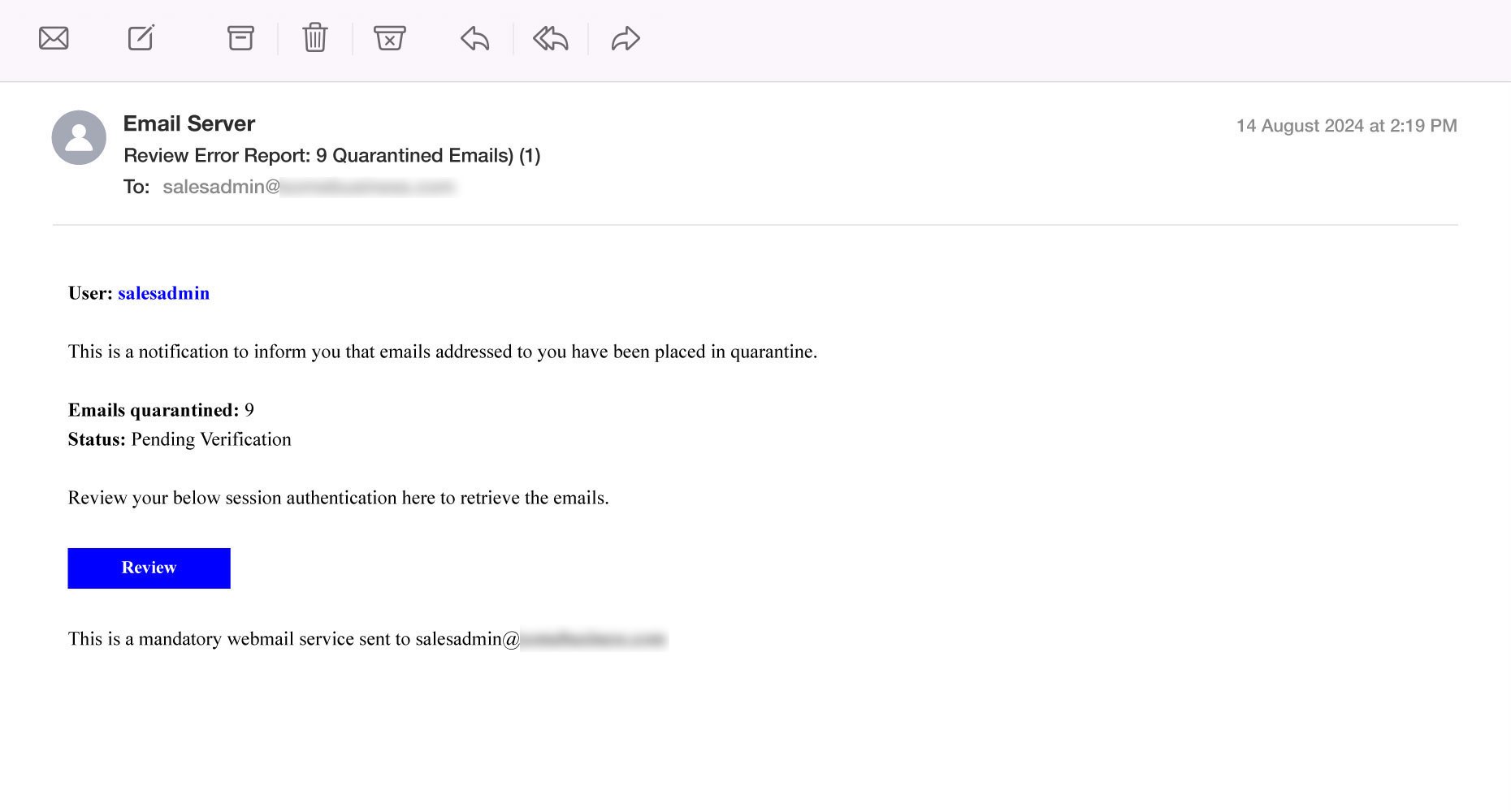
Background: Many email systems, especially those used by businesses and organizations, have built-in spam filters that automatically quarantine or hold potentially dangerous emails. These emails are flagged because they contain suspicious links, attachments, or other characteristics indicative of phishing or malware. Legitimate quarantine notifications typically inform users of the email being flagged and may provide a secure link to view or release the message.
How Scammers Use It: Scammers exploit the quarantine notification process by sending fraudulent emails that appear to be from the email service or security system of the recipient’s organization. These emails claim that a message has been quarantined or flagged for review, often suggesting that the user needs to click a link to retrieve or release the email. The link, however, directs to a phishing site designed to steal login credentials, install malware, or collect other sensitive information.
How to Detect:
- Carefully verify the sender’s email address. Genuine quarantine notifications usually come from a trusted domain.
- Check for signs of a phishing attempt, such as poor grammar, a sense of urgency, or requests for personal or login information.
- If in doubt, contact your organization’s IT department or security team to confirm whether the notification is legitimate.
8. Fake Meeting Invites
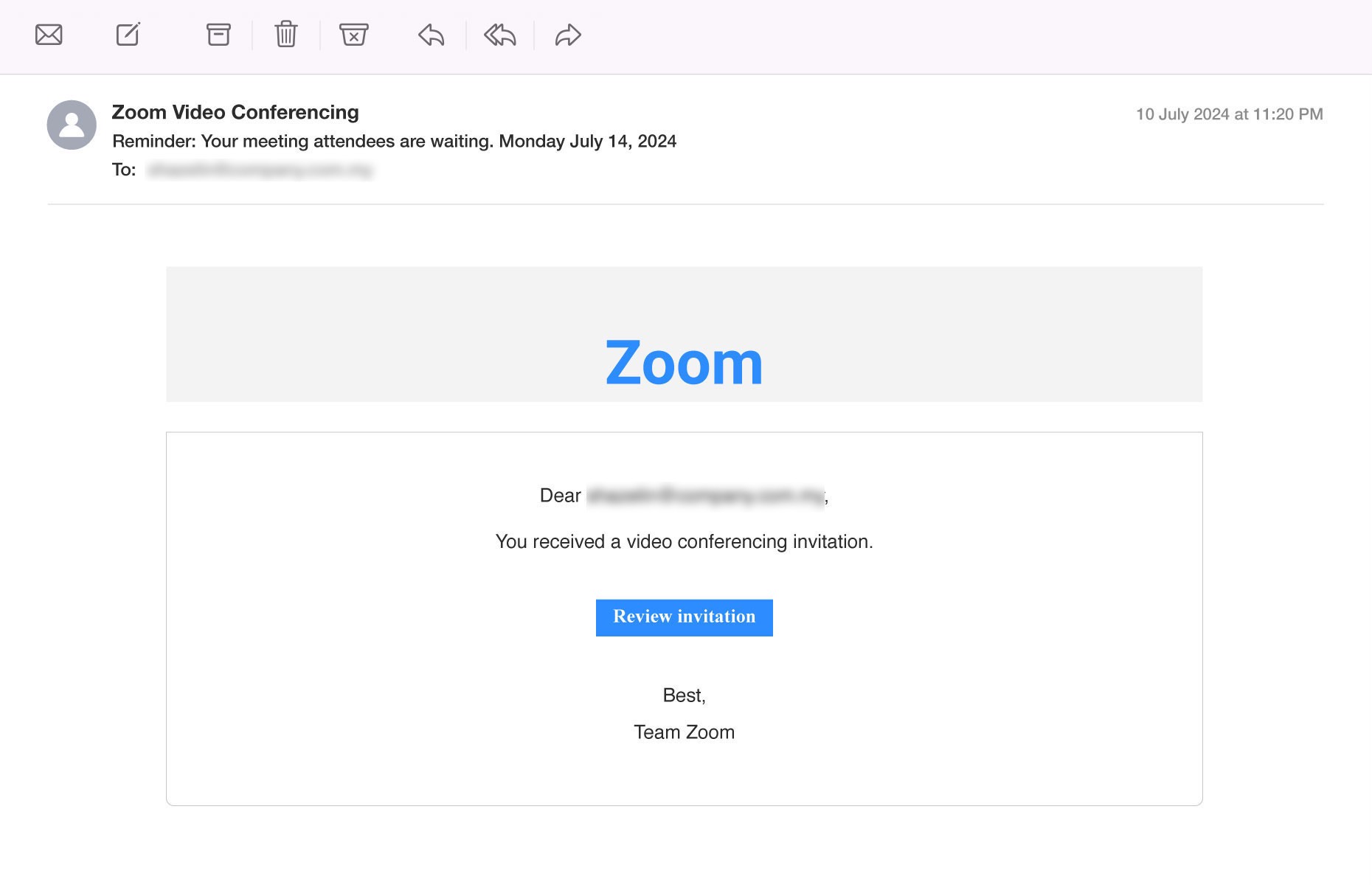
Background: Online meeting platforms like Zoom are commonly used for personal and business communication, offering easy access to virtual meetings, webinars, and conferences. Legitimate meeting invites typically include a unique link to a scheduled session, along with details such as the meeting ID, password, and time. These invites are sent directly from the platform or a recognized host.
How Scammers Use It: Scammers take advantage of the widespread use of video conferencing tools like Zoom to send fake meeting invites. These fraudulent emails often appear to come from trusted sources, such as a colleague or an important client, and contain a link to “join a meeting” or “review invitation”.
How to Detect:
- Double-check the sender’s email address. Scammers often use email addresses that look similar but have small differences from legitimate domains.
- Hover your mouse over any links before clicking to check the URL. It should direct to the official Zoom domain (zoom.us) or the trusted host’s website.
- If the invite seems suspicious or if you weren’t expecting the meeting, reach out to the host or sender using their official contact details to confirm the legitimacy of the invite.
9. Impersonated Executive Emails (CEO Fraud)
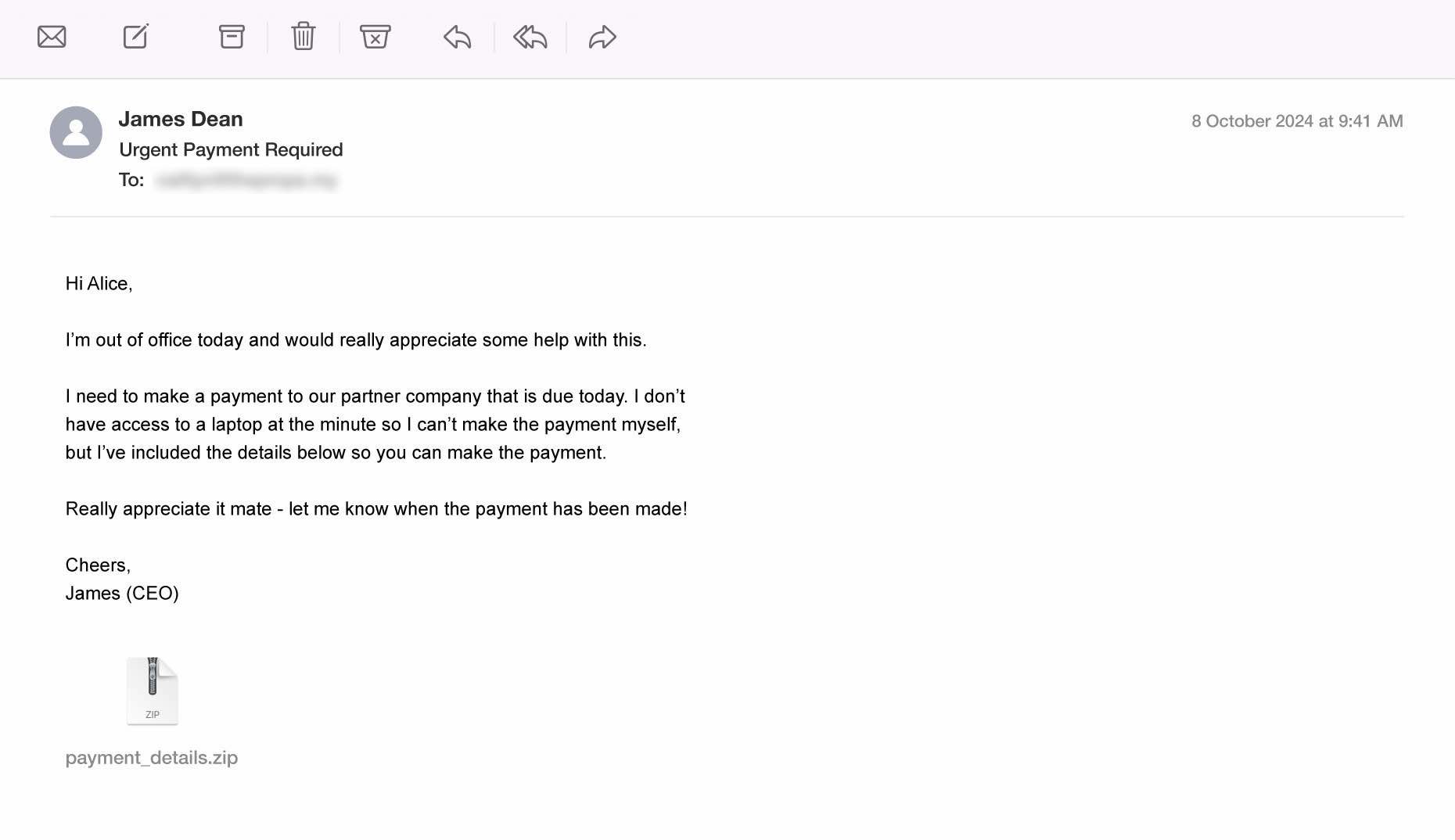
Background: CEO fraud, also known as Business Email Compromise (BEC), occurs when a scammer impersonates an executive — often the CEO, CFO, or other high-level officer — to manipulate employees into performing fraudulent actions. These actions might include transferring money, providing sensitive company information, or altering payment details.
How Scammers Use It: Scammers impersonate high-ranking executives, often using email addresses that closely resemble those of legitimate company executives (e.g., using slight variations in the domain name). The email usually carries a sense of urgency, instructing the employee to transfer funds, share sensitive information, or change payment details. The email may seem genuine, featuring official company logos and terminology to build trust.
How to Detect:
- Scrutinize the sender’s email address for minor inconsistencies (e.g., incorrect domains or letters swapped). Genuine emails from the CEO or executives should come from company domains.
- Be wary of emails requesting wire transfers, changes to financial accounts, or other urgent financial tasks, especially if they seem unusual or out of the norm.
- If you receive an unexpected or urgent request from an executive, verify it by contacting them directly through a separate communication channel (e.g., a phone call or a direct message).
10. False Job Opportunity Offers
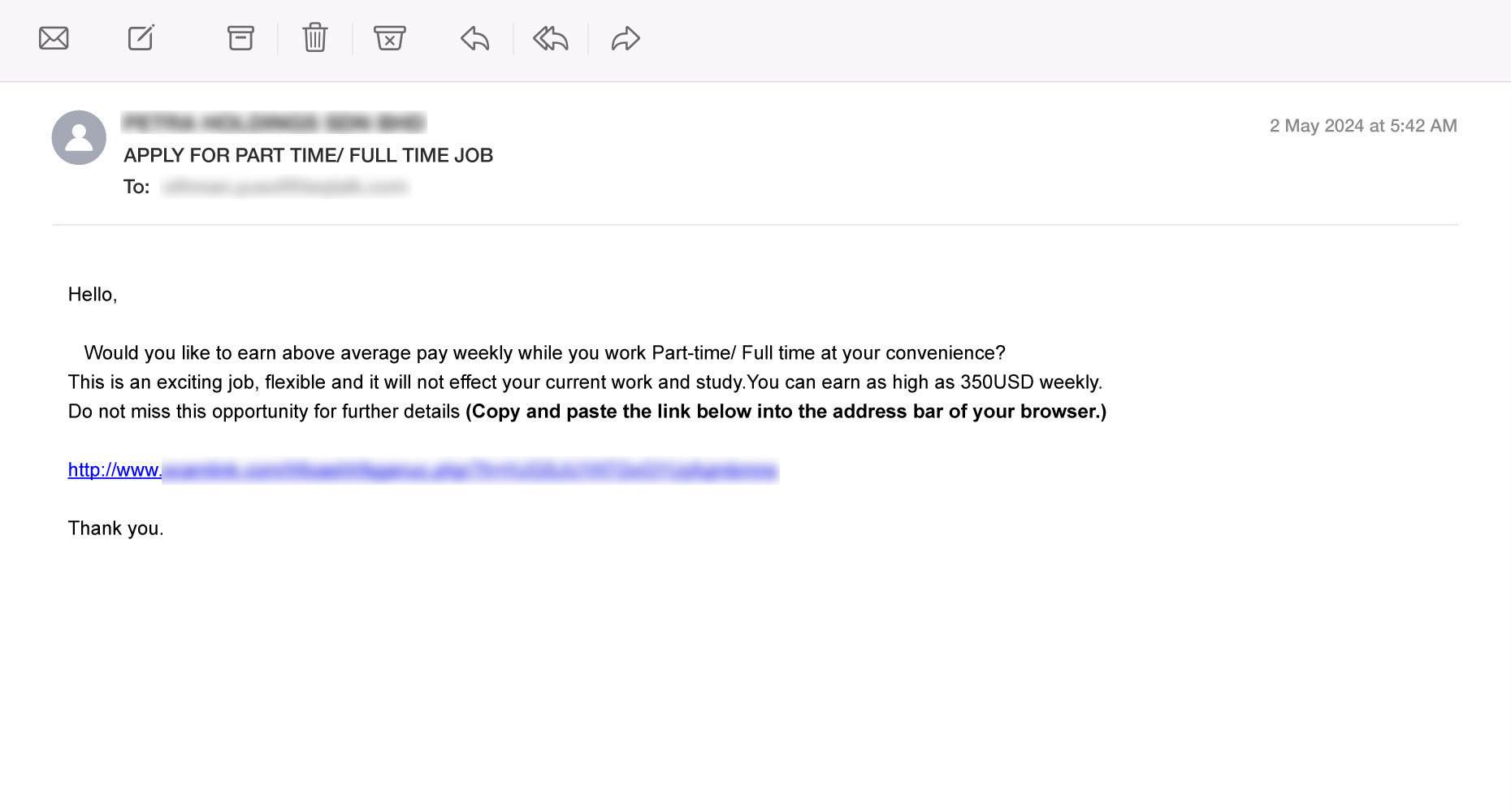
Background: Job offers are commonly sent to applicants who have applied for positions or signed up for job alerts through legitimate platforms. These communications typically include details about the company, position, salary, and next steps in the hiring process. Legitimate job offers are usually followed up with interviews, either in person or virtually, where candidates can ask questions and confirm the details of the offer.
How Scammers Use It: Scammers exploit the job market by creating fake job opportunities that seem too good to be true. These fake job offers typically appear in unsolicited emails that promise high salaries, flexible hours, and other attractive benefits, often with minimal experience required. The fake company may have a convincing name, logo, and website that closely resembles a legitimate organization to build trust.
How to Detect:
- Be cautious of job offers that promise unusually high salaries for minimal work or experience. Legitimate job opportunities will have compensation in line with industry standards.
- Verify the legitimacy of the company by researching it online. Look for official websites, LinkedIn profiles, or reviews from other employees.
- Never pay for a job, training, or application fee in advance. Legitimate employers do not ask candidates for money.
Wrapping Up
Phishing emails may appear legitimate, but they often contain malicious links or attachments designed to steal sensitive information. Always be cautious when receiving unsolicited emails, and verify any requests for personal information by contacting the organization directly through official channels. To learn more about identifying phishing emails, check out these tips and test your knowledge with the quiz.