Home > Empowering Tips > 8 Examples of Common Phishing Emails

Phishing comes from the word fishing: the hacker lures users with a “bait” (legitimate-looking email, text message or website), hoping that users will “bite” by providing their sensitive information such as username, password and bank information, or by downloading malicious software that infects the user’s computer.
Here are 8 examples of common phishing emails for your reference so that you can identify and avoid them when you receive one.
Account Suspension Mail
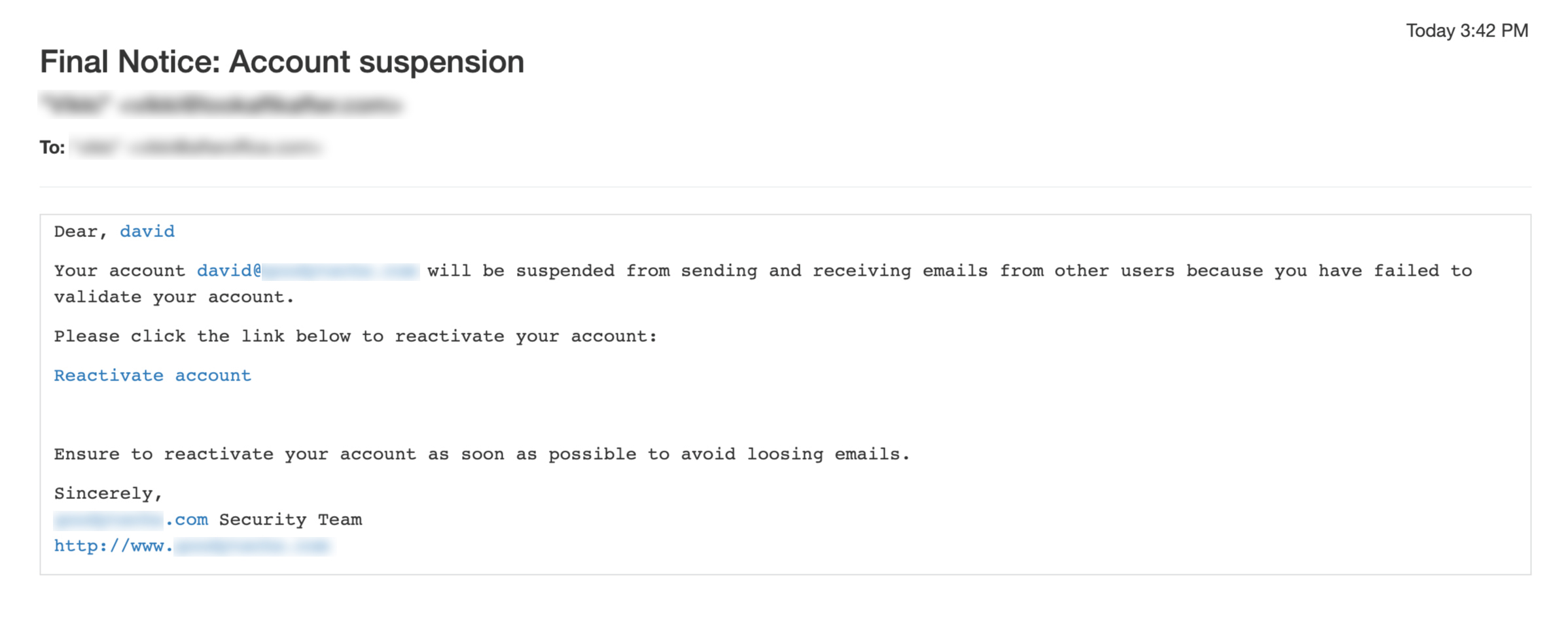
Account suspension email is one of the most popular phishing templates that scammers use these days. They pretend to be from your service provider or IT administrator, and claim that your account will be suspended unless you click a link to reactivate your account. They ask for your personal information like username and password. The link also often contains virus that could infect your computer.
How to detect:
- Take note on the sender’s actual email address. Scammers may use your domain in their name to appear legitimate, but the email address may be from an external domain.
- Look for forceful wording like “Final Warning” and “Final Notice” in the subject line, which is a common scare tactic used by most phishing scams.
- Hover over the link in the email without clicking it. If it does not match the context, it is most probably a malicious link. Beware of slight alterations to URLs, for example, https://legitimatesite.com might appear as http://legitmatesite.com.
Password Expiration Notice
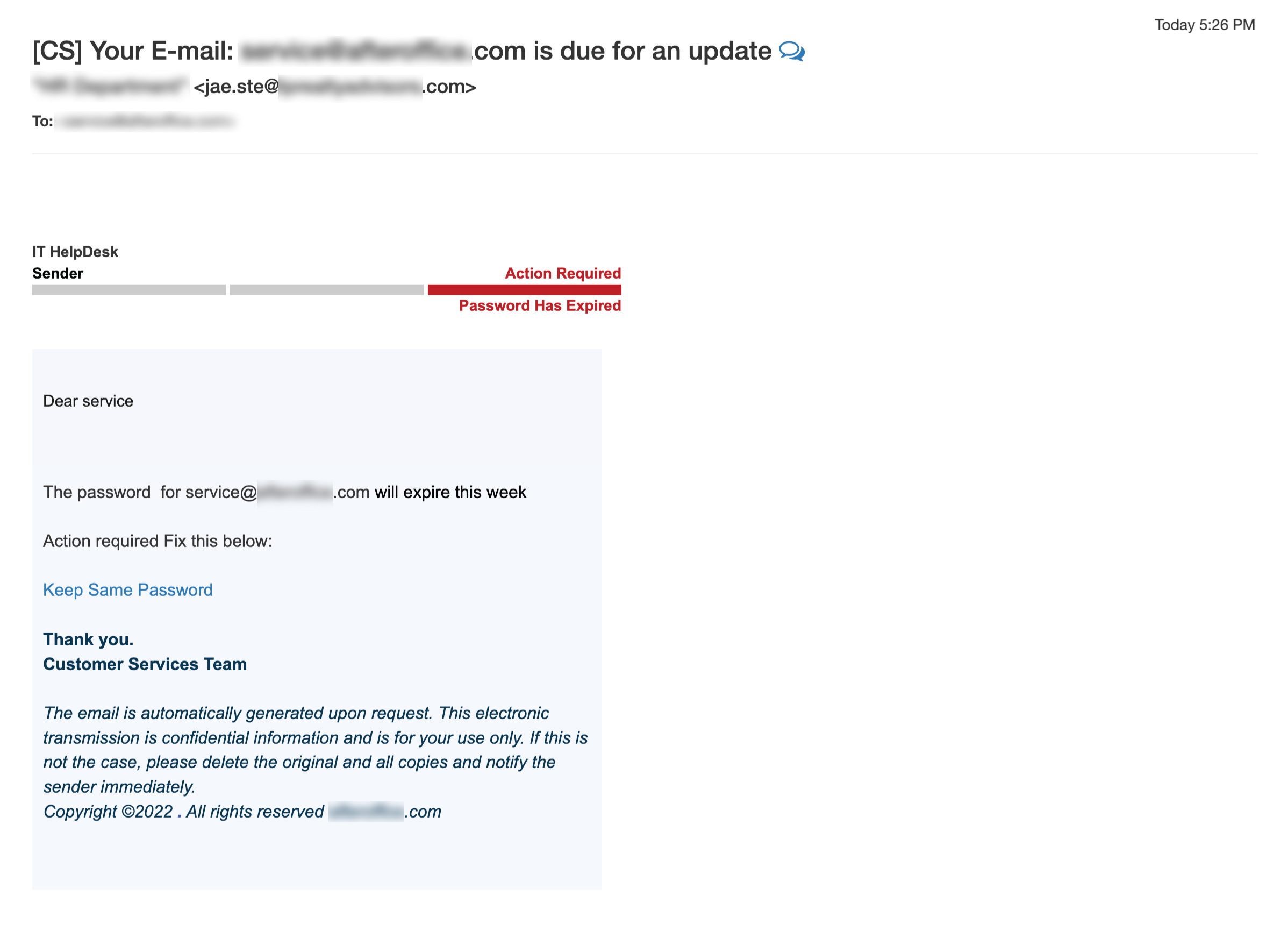
Similar to the sample above, this type of phishing email claims that your password has expired. You will be asked to click the link inside the email, which will direct you to a seemingly legitimate webpage to update your password. However, any credentials entered into this page will fall straight into the hands of the hacker, who will then use your account to perform illegal activities (like sending spams, delivering malware, stealing your email data, etc).
How to detect:
- Check who send the email. If the sender is unknown or suspicious-looking, it is a scam.
- Look for grammar mistakes or abnormal sentences. For example, “Action required Fix this below” in one sentence does not make sense.
- Check the URL before clicking it. Never click the link if it is pointing to an unknown website.
- Beware of sender who requests for your password.
Fake Mailbox Full Notice
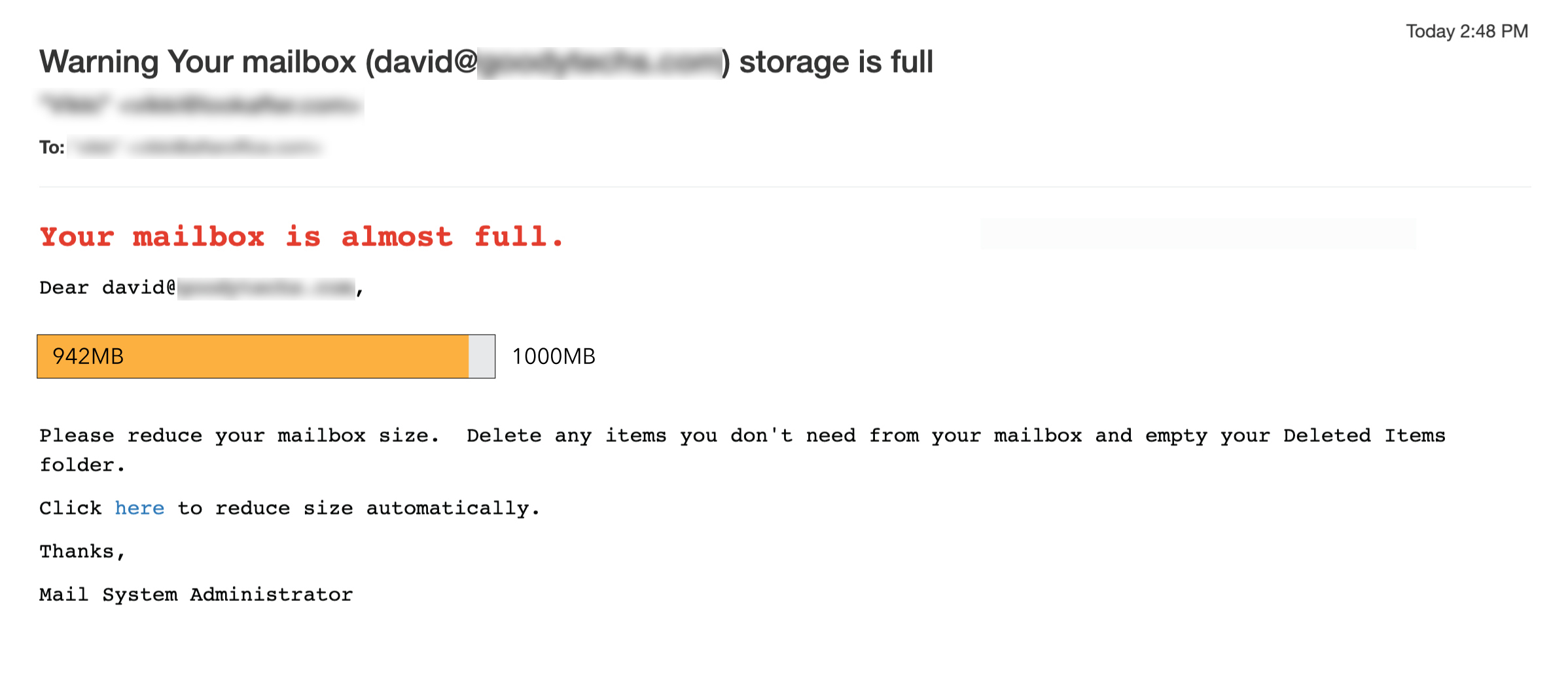
Another example of phishing email is the fake mailbox full notification email. This type of scam mail urges you to click a button or link to reduce your mailbox size automatically. If you click the button or link, a malware will be downloaded, infecting your computer.
How to detect:
- Check if the sender email address is related to your domain or email service provider. If you do not recognize the sender email address, you should be aware of the email.
- Hover over the link to check the target URL. If it is pointing to a website that has nothing to do with your website (or your email service provider’s website), discard the email immediately.
- Email provider usually does not request user to clear storage space by clicking a URL link within an email. All email space adjustment should be configured by the administrator through official admin portal.
Bank Scam Email
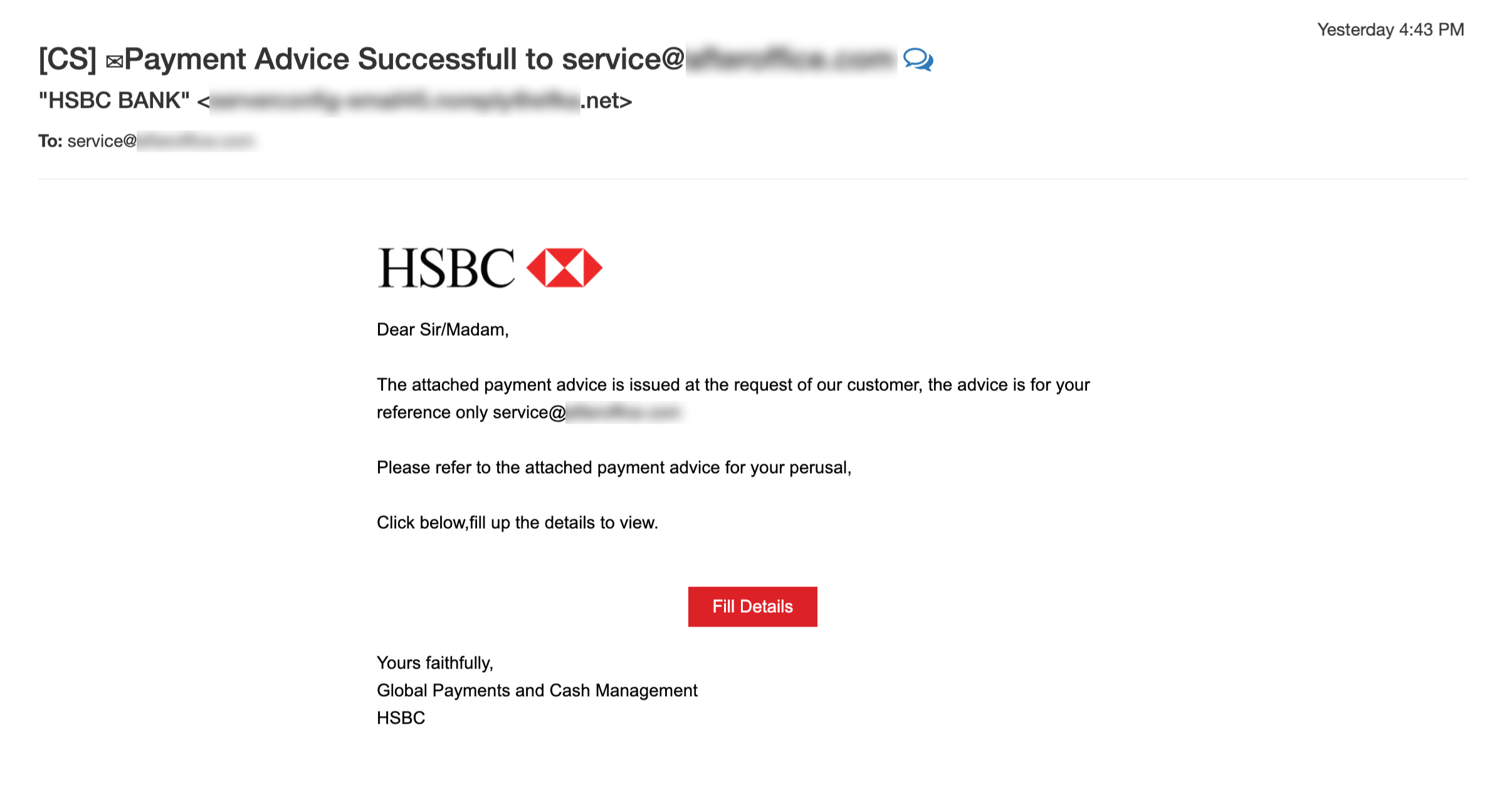
People tend to be more attentive towards emails sending from banks. Hackers take advantage of this by impersonating your bank, sending you fraudulent emails related to bank transactions and withdrawals. Their goal is to obtain your sensitive information like account information and password, which they can use to steal your funds or perform unauthorized transactions.
How to detect:
- Make sure the sender email address does come from your bank’s official domain. Take note on any extra or missing character in the email address. You should verify with the bank’s customer service if you are unsure of the email.
- Look for grammar mistakes in the email message. If it contains spelling errors or unusual language, it is most likely a scam mail, because legitimate companies never risk making a bad impression with poor grammar.
WeTransfer Phishing Mail
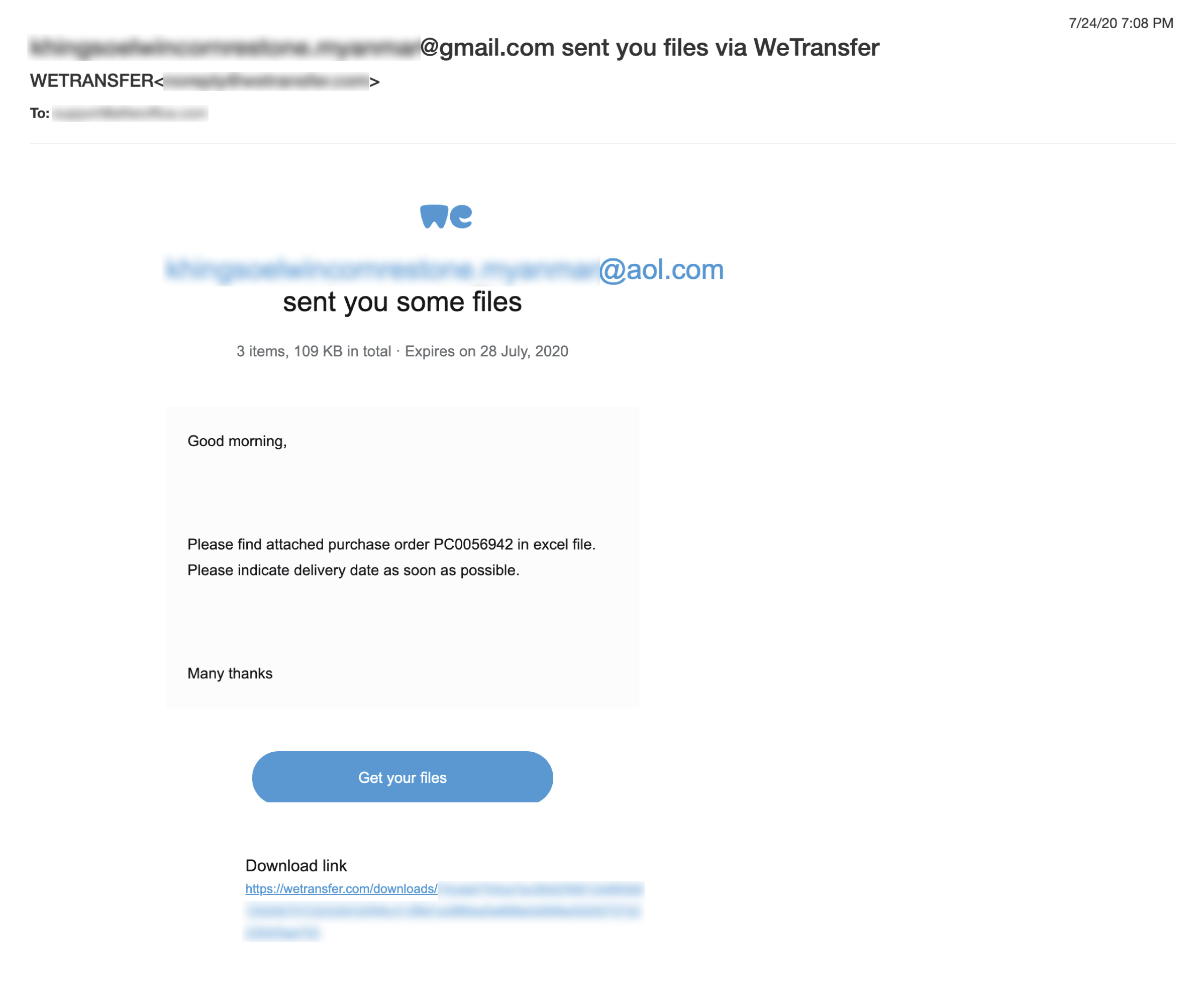
WeTransfer is one of the popular cloud-based online platforms for file transferring. Due to its popularity, cybercriminals would take the opportunity to deceive you through this medium. The WeTransfer phishing mail looks very similar to the normal WeTransfer email, as if someone has sent you a file through WeTransfer, where you need to click a link to get the file. Many times, the link contains malware, and when it is clicked, you will be asked for your personal information.
How to detect:
- Look out for suspicious download URL. Hover over the button or link to view the actual URL. Any URL that is not part of https://wetransfer.com should be considered dangerous.
- Look at the sender – “WeTransfer” may be presented as the sender’s name, but the email address may be from an unknown source.
- If you do not expect any file transfer from anyone, you can simply ignore the email as it is probably a phishing attempt. Even if you are expecting a file transfer via WeTransfer, do confirm the file name and size with the sender before interacting with the email.
Unusual Activity Notice
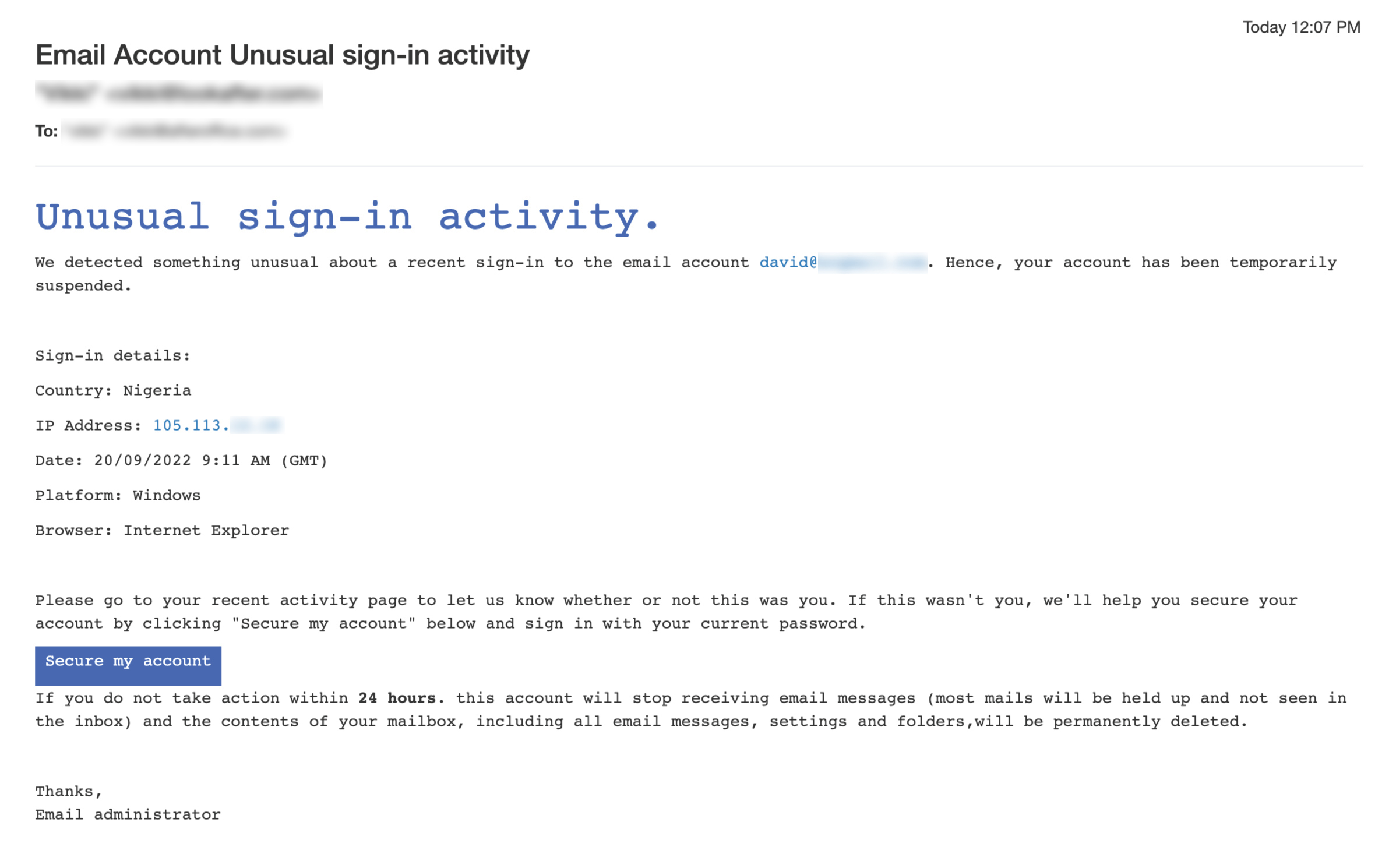
People are most likely alerted when they receive information related to the security of their account. Knowing this, cybercriminals forge emails about security breach, with fake sign-in details such as IP address, country, date and/or web browser and send to users. Users are usually asked to secure their account by clicking a link or button present in the email. If you click the link or button, you will be navigated to a fake website that asks for your information (like username and password). If you provide these information, the hacker will gain access to your account.
How to detect:
- Check the sender address. If the email address looks legitimate, check for any extra or missing characters in the sender email or domain.
- Spot for any urgency and threatening tone, such as “If you do not take action in 24 hours, your account will be suspended”.
- Check the URL of the button before clicking it. If the URL is linking to a suspicious-looking website, it is a scam.
- Never provide your password to any email sender who asks for it.
Quotation Request Scam
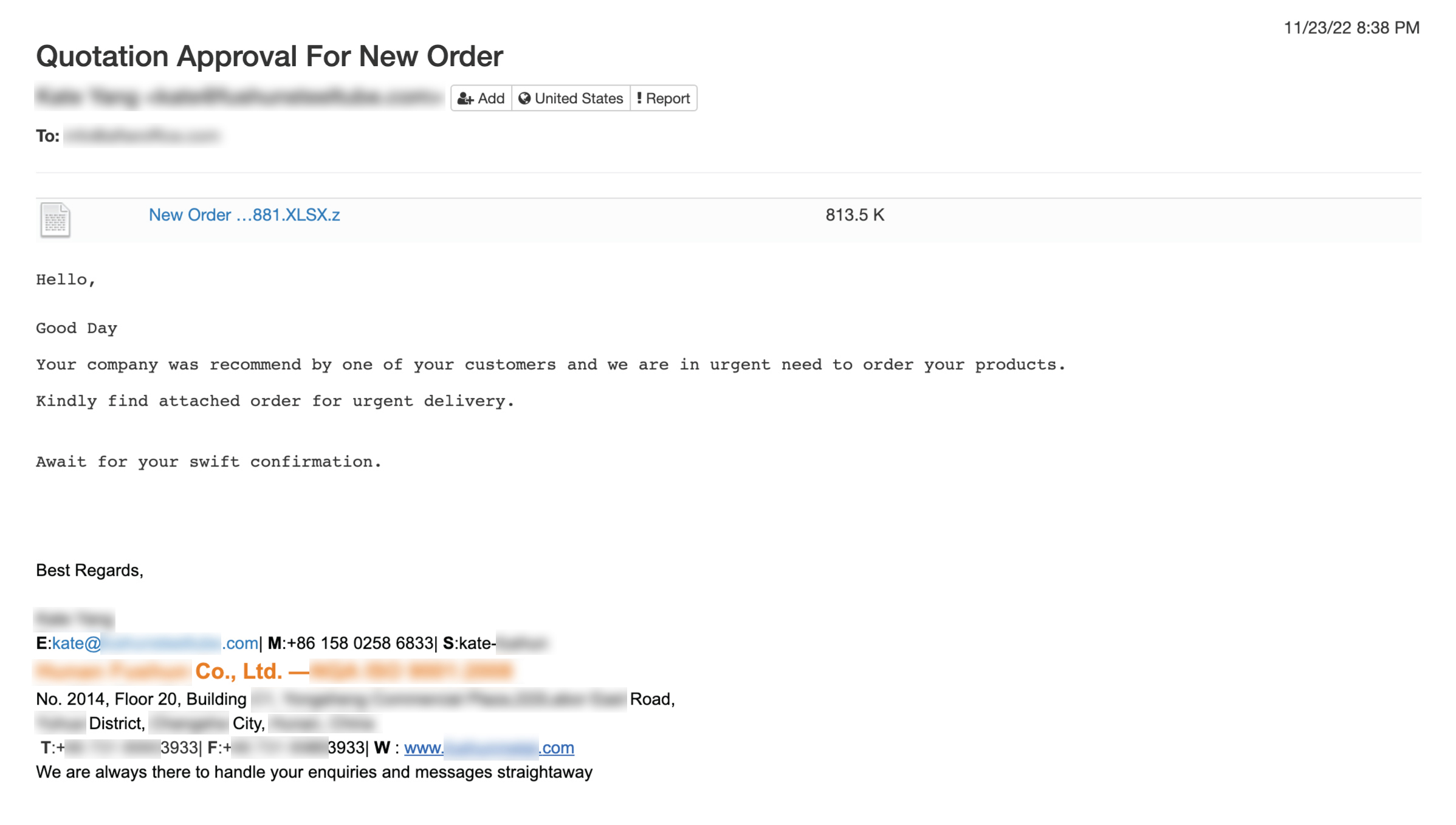
In this kind of scam, the fraudster requests to order products from your company and asks for a quote by attaching a purchase order. The attached file is usually in PDF, Document, compressed or unknown file format, which contains malicious code that could corrupt your computer if it is downloaded.
How to detect:
- Never respond to or download any attachment from emails that are sent from unknown senders.
- If the attachment is in unusual format or is compressed (in .zip, .rar, etc), do not download it.
- Look for vague content in the message, such as “we are in urgent need to order your products” – any legitimate customer should include the actual product or service name or details when asking for quotation.
Human Resource (HR) Email Scam
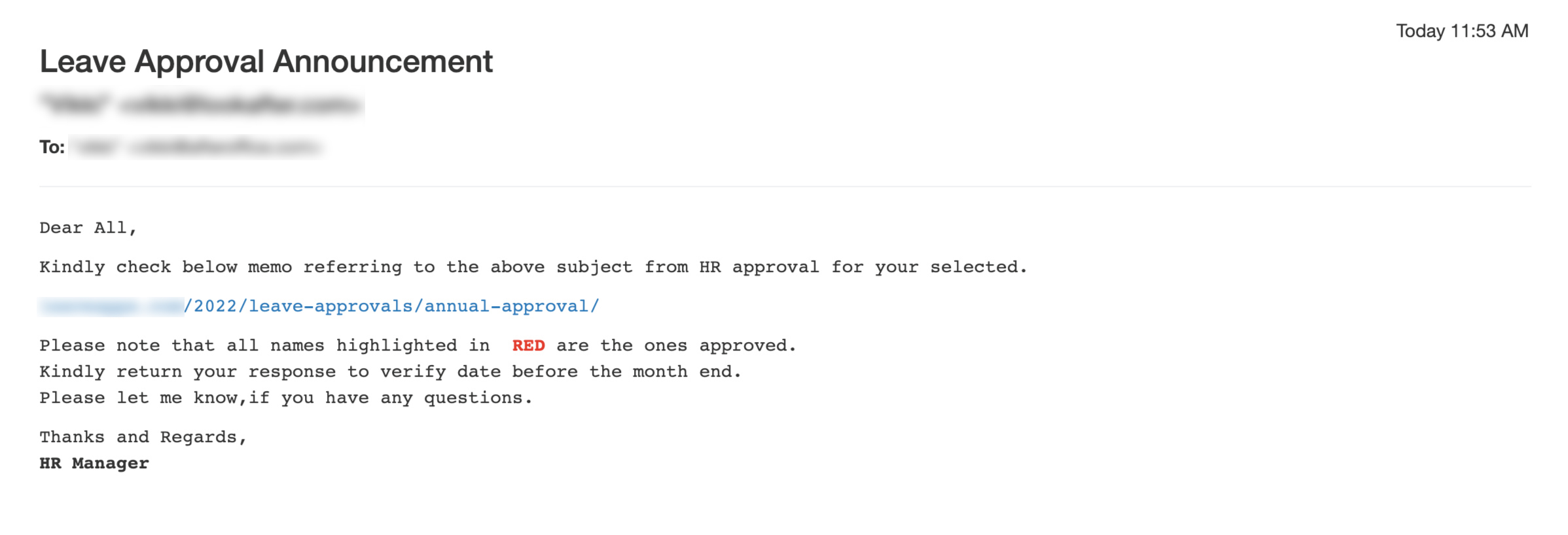
In such scam, the hacker disguises as your Human Resource (HR) department that sends you a link to check about HR-related matters like leave approvals. Clicking the link leads you to a phishing website that requests you to sign in – which is the hacker’s purpose – to steal your username and password.
How to detect:
- Emails that are sent from your HR department should come from your own domain. Any HR-related email that comes from an external domain is most probably a scam mail.
- Double-check with your HR department if the email was really sent from them.
If you detect any suspicious email, it is best to remove it immediately from your mailbox. Never respond to it till you are 100% sure about its authenticity. If you need help identifying an email, you can always reach out to your email service provider for verification.