Home > Empowering Tips > Email Spoofing: How do attackers spoof an email address?

Email spoofing is a method that cybercriminal uses to trick you into thinking that an email is sent from someone you know or trust, such as your customer, supplier, colleague, or an authorized bank. It is often used in phishing attacks, designed to take over your account, send viruses, steal sensitive information or money.
Email spoofing may sound like a sophisticated technique, but it is actually rather simple. It does not require hacking into an account. Instead, it involves modifying the email headers to look like they are coming from a legitimate entity, by using a look-alike email address, or a similar email format (e.g. signature).
Spoofed emails can be dangerous and damaging if you are unfamiliar of how to identify one. Here are common types of email spoofing that you should be aware of if you receive one.
Spoofing via display name
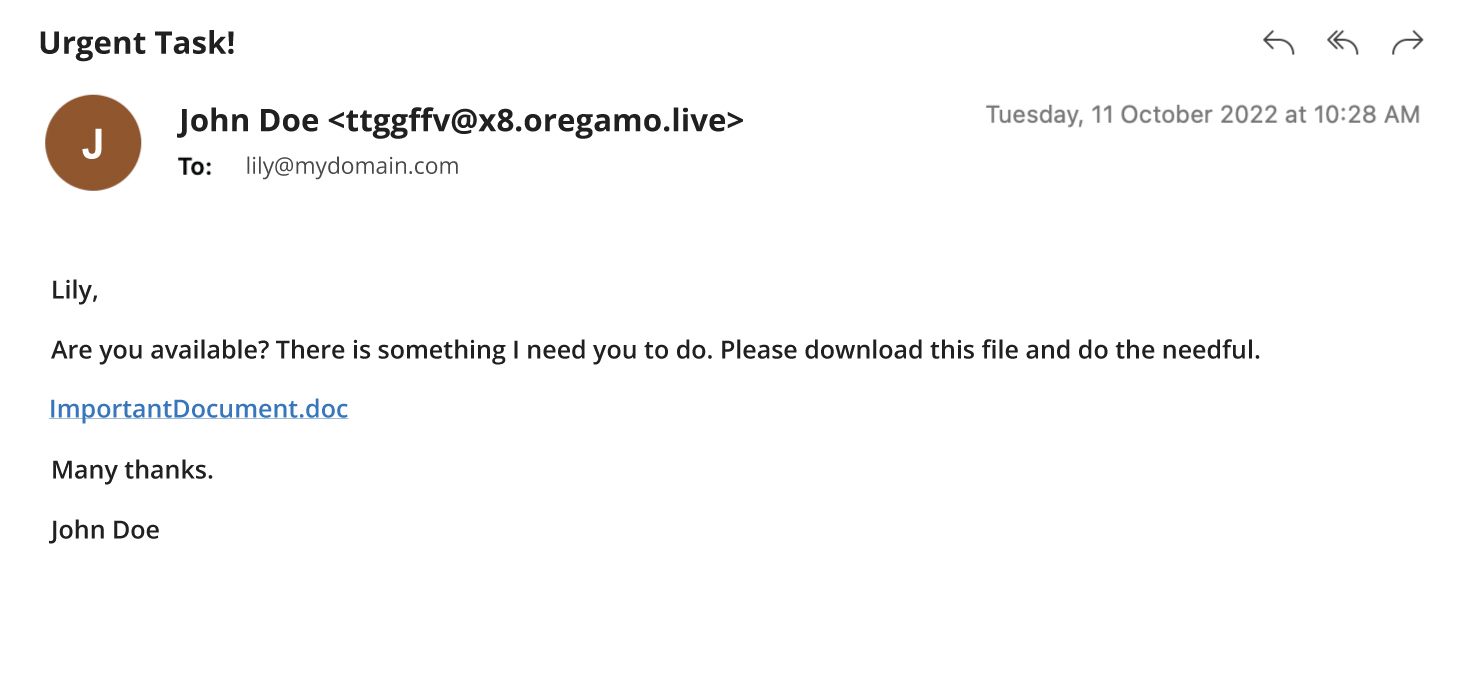
Display name spoofing involves forging of the email sender’s display name. Hackers can do this by registering a free email address and use the same name as your contact. To further convince you, some may use your contact’s full domain or email address as the sender’s name.
For example, Lily receives an email seemingly sent from her colleague, John Doe, but the mailto: is displaying an entirely different email address.
This type of spoofed email will bypass all spoofing security measures and spam checks because it comes from a legitimate email address. Moreover, the design of many modern and mobile email client applications displays only the sender’s name, making it harder for users to spot the spoofed identity.
Spoofing via lookalike domains
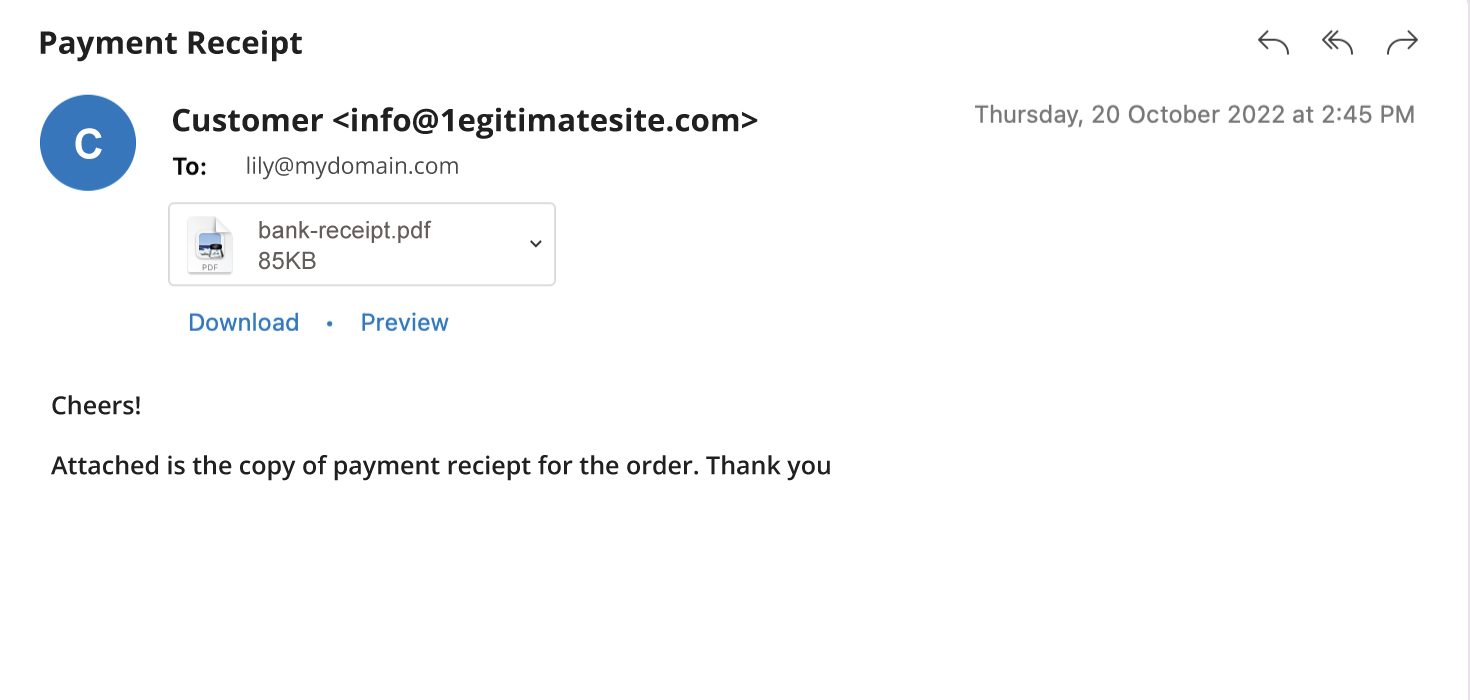
In this type of spoofing, the hacker registers and uses a domain that is similar to the impersonated domain, e.g. “@1egitimatesite.com” instead of “@legitimatesite.com”. The change could be too small to be noticed by the recipient.
This type of spoofing will also bypass spam filters as the email address is legitimate. The only way to avoid such spoofing is to look closely to the email address and spot any subtle differences.
Spoofing via legitimate domains
Fundamentally, emails are relayed through Simple Mail Transfer Protocol (SMTP), which does not require any authentication. Hackers may take advantage of this vulnerability and use a trusted email address in the From header. Domains that are not employed with verification and authentication countermeasures (e.g. SPF, DKIM, DMARC) may be misused for such spoofing.
Hackers may also use compromised SMTP servers, or set up malicious SMTP servers for this approach.
In the fight against email spoofing, prevention is better than cure.
As an email user, recognizing and avoiding spoofed emails are the first key steps to safety. If you receive a seemingly legitimate email that looks suspicious, don’t trust it immediately. Verify with the sender in person or your email provider before responding to the email.